[ad_1]
The TeaBot Remote Access Trojan (RAT) has been upgraded, leading to a huge increase in both targets and spread worldwide.
On March 1, the Cleafy research team said TeaBot now targets over 400 applications, pivoting from an earlier focus on “smishing” to more advanced tactics.
Smishing attacks are used to compromise mobile handsets via spam text messages containing malicious links. It is often the case that these links — pretending to be from your bank, social media network, or a delivery company, for example — will lead victims to fraudulent websites that request their personal data and account credentials.
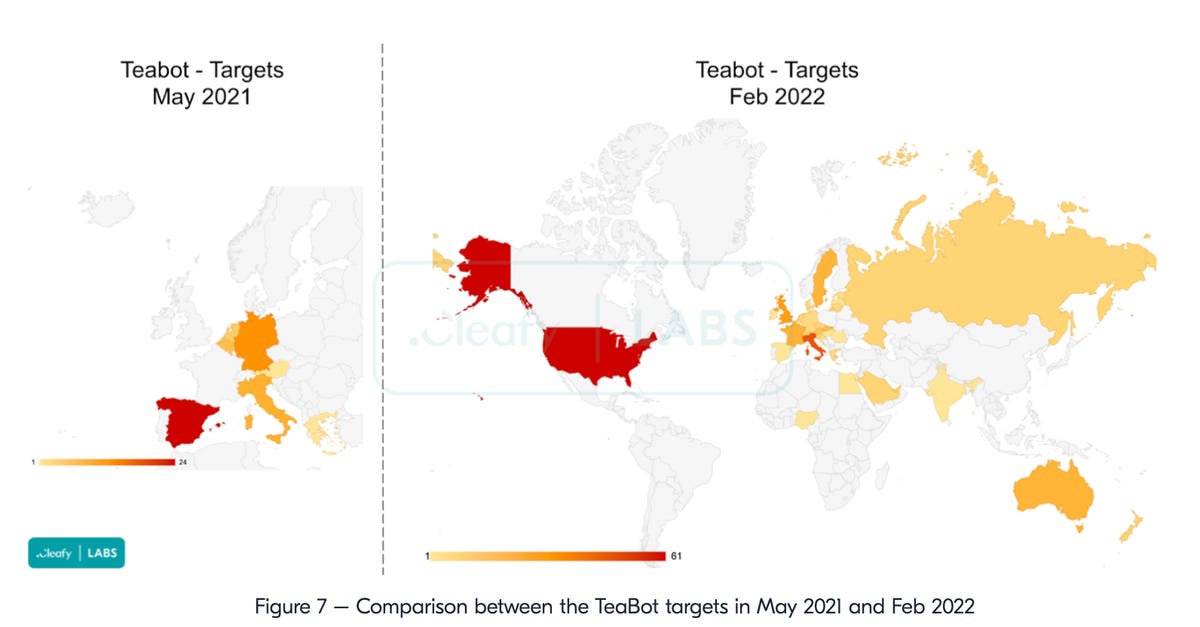
When TeaBot emerged at the beginning of 2021, the malware, also known as Toddler/Anatsa, was distributed via smishing and had a list of only 60 lures, including TeaTV, VLC Media Player, DHL, and UPS.
Further research conducted by PRODAFT in July 2021 found that while TeaBot had been configured to strike “dozens” of European banks, successful attacks were traced to 18 financial organizations.
At the time, 90% of TeaBot infections were connected to only five of these companies, leading the researchers to suspect a successful SMS-based phishing campaign was responsible.
TeaBot has migrated from Europe to include new countries, such as Russia, the US, and Hong Kong, and is using an expanded target list beyond online services — banks, cryptocurrency exchanges, and digital insurance providers are now also being impersonated in phishing attempts.
Cleafy
Risk management firm Cleafy says the malware has also managed to infiltrate official Android repositories through dropper apps.
In samples obtained in February by the company, an app published to Google Play, “QR Code & Barcode Scanner” was found to serve TeaBot to users through a fake update.
There is a common tactic by malware developers: publish a legitimate application to an official app repository, clear existing security checks, and then once a large user base has been established — in this case, over 10,000 people — then deploy an update that turns the software malicious.
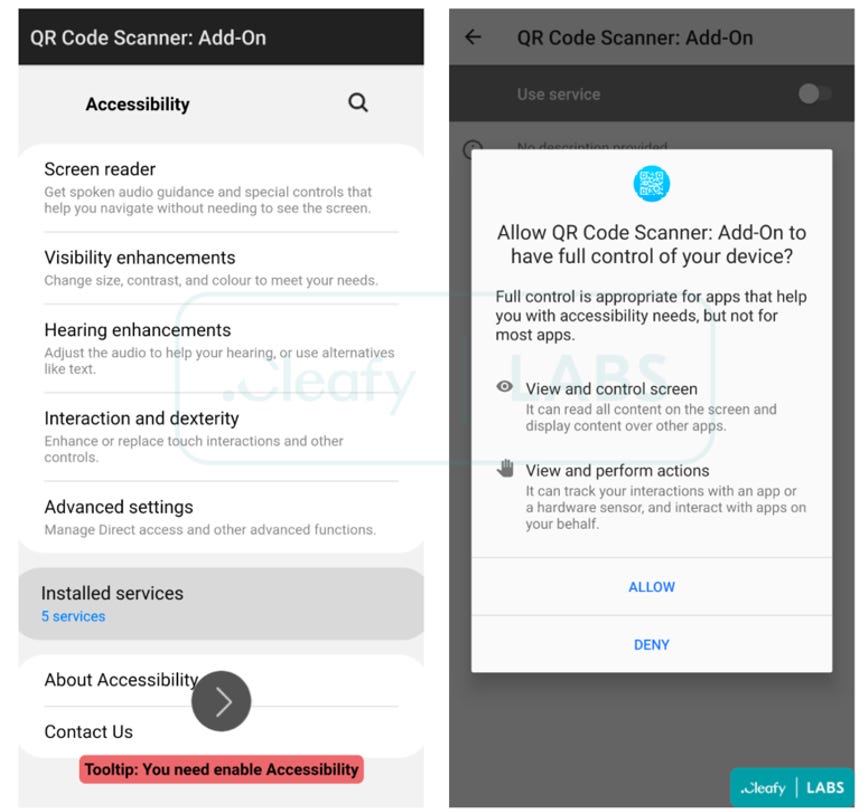
In TeaBot’s case, the fake update/dropper will request permission to download a second application, “QR Code Scanner: Add-On,” that contains the RAT.
Cleafy
This app is downloaded from one of two GitHub repositories owned by the same developer.
Once installed, TeaBot will first abuse the Android OS’ Accessibility services, requesting permissions that allow the malware to perform activities including keylogging and remote device hijacking.
Furthermore, TeaBot will grab screenshots and monitor the handset’s screen to steal credentials including account information and two-factor authentication (2FA) codes.
“Since the dropper application distributed on the official Google Play Store requests only a few permissions and the malicious app is downloaded at a later time, it is able to get confused among legitimate applications and it is almost undetectable by common AV solutions,” Cleafy warns.
ZDNet has reached out to Google and we will update when we hear back.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
[ad_2]
Source link

