[ad_1]
Researchers have found almost 100,000 new variants of mobile banking Trojans in just a year.
As our digital lives have begun to center more on handsets rather than just desktop PCs, many malware developers have shifted part of their focus to the creation of mobile threats.
Many of the traditional infection routes are still workable – including phishing and the download and execution of suspicious software – but cyberattackers are also known to infiltrate official app stores, including Google Play, to lure handset owners into downloading software that appears to be trustworthy.
This technique is often associated with the distribution of Remote Access Trojans (RATs). While Google maintains security barriers to stop malicious apps from being hosted in its store, there are methods to quietly circumvent these controls.
In 2021, for example, Malwarebytes found an app in Google Play disguised as a useful barcode scanner with over 10 million active installs. While the app was submitted as legitimate software, an update was issued to the software after it had accumulated a huge user base turning the app into an aggressive adware nuisance.
The same tactic can be used to turn seemingly benign apps into banking Trojans designed to steal your financial data and account credentials from online services. In the mobile world, theft can occur by redirecting users to phishing pages or by performing overlay attacks, in which a phishing window covers a banking app’s display. Trojans may also quietly sign up their victims to premium telephone services.
Recent examples of Trojans ending up in Google Play include Joker and Facestealer.
According to new research published by Kaspersky, 97,661 new mobile banking Trojan variants were detected in 2021, alongside 17,372 new mobile ransomware Trojans and a total of 3,464,756 malicious installation packages, .APKs that can be installed on jailbroken devices or those that accept apps from unknown developers.
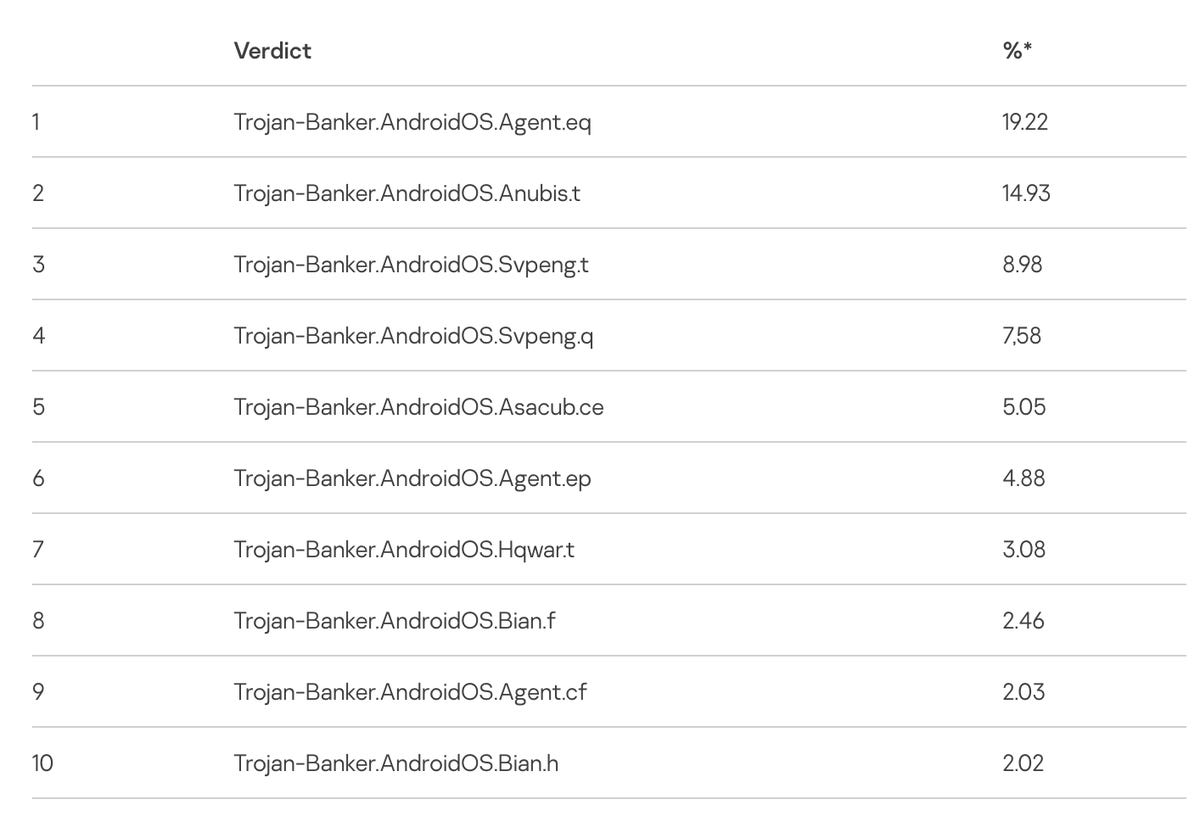
The banking Trojans responsible for the most detected attacks over 2021 were Trojan-Banker.AndroidOS.Agent, Trojan-Banker.AndroidOS.Anubis, and Trojan-Banker.AndroidOS.Svpeng.
Kaspersky
Residents of Japan, Spain, Turkey, France, Australia, Germany, Norway, Italy, Croatia, and Austria are most commonly targeted by mobile banking Trojans.
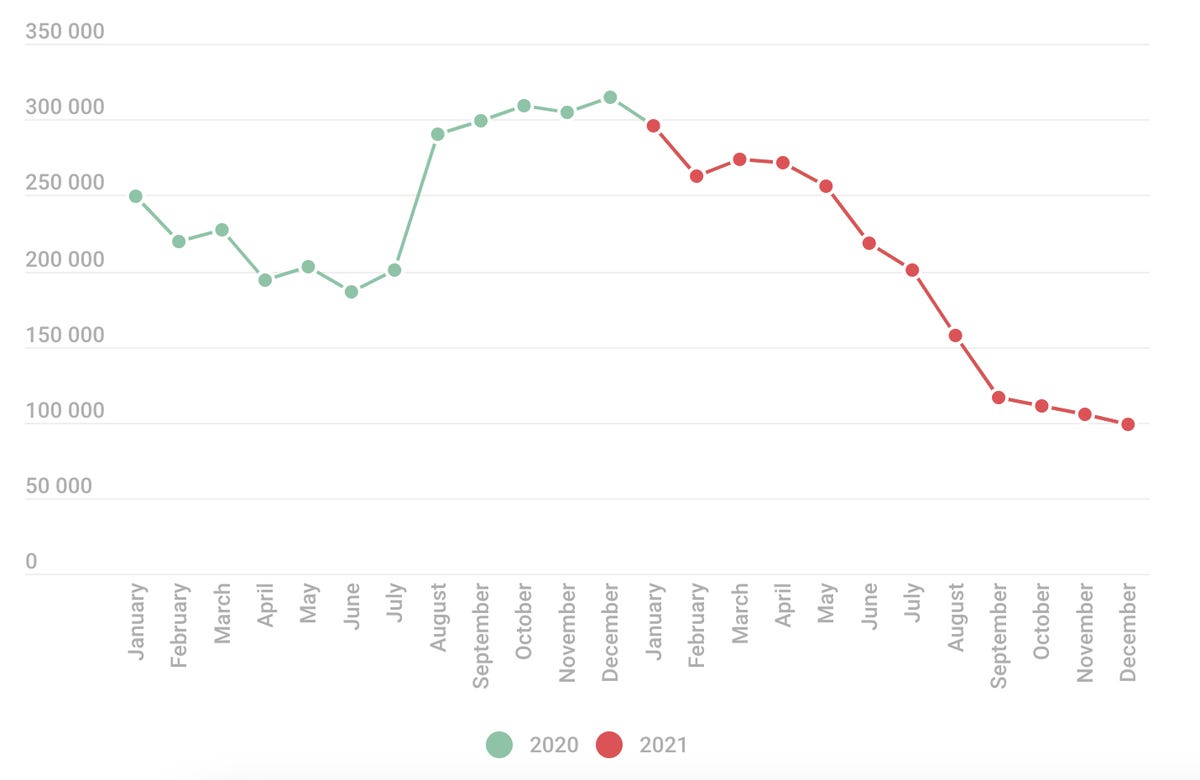
Kaspersky says that after a steep climb in the number of attacks detected in 2020, banking Trojan rates are now on the decline.
Kaspersky
The cybersecurity researchers added that there is a “downward” trend on mobile attacks in general, but “attacks are becoming more sophisticated in terms of both malware functionality and vectors.”
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
[ad_2]
Source link

