[ad_1]

A hands-on guide
If your PC were lost or stolen, you’d probably cringe at the cost of replacing it. But that’s nothing compared to what you’d stand to lose if someone had unfettered access to the data on that device. Even if they can’t sign in using your Windows user account, a thief could boot from a removable device and browse the contents of the system drive with impunity.
The most effective way to stop that nightmare scenario is to encrypt the entire device so that its contents are only available to you or someone with the recovery key.
All editions of Windows 10 and Windows 11 include XTS-AES 128-bit device encryption options that are robust enough to protect against even the most determined attacks. Using management tools, you can increase the encryption strength to XTS-AES 256.
On modern devices, the encryption code also performs pre-boot system integrity checks that detect attempts to bypass the boot loader.
BitLocker is the brand name that Microsoft uses for the encryption tools available in business editions of Windows (desktop and server). A limited but still effective subset of BitLocker device encryption features is also available in Windows 10 and Windows 11 Home editions. Here’s how to make sure your data is protected.
What are the hardware requirements for BitLocker?
The most important hardware feature required to support BitLocker Device Encryption is a Trusted Platform Module chip, or TPM. The device also needs to support the Modern Standby feature (formerly known as InstantGo).
Virtually all devices that were originally manufactured for Windows 10 meet these requirements. All devices that are compatible with Windows 11, without exception, meet these requirements.
How does BitLocker work in Windows 10 and Windows 11?
On all devices that meet the BitLocker hardware requirements (see the following section for details), device encryption is automatically enabled. Windows Setup automatically creates the necessary partitions and initializes encryption on the operating system drive with a clear key. To complete the encryption process, you must perform one of the following steps:
- Sign in using a Microsoft account that has administrator rights on the device. That action removes the clear key, uploads a recovery key to the user’s OneDrive account, and encrypts the data on the system drive. Note that this process happens automatically and works on any Windows 10 or Windows 11 edition.
- Sign in using an Active Directory account on a Windows domain or an Azure Active Directory account. Either configuration requires a business edition of Windows 10 or Windows 11 (Pro, Enterprise, or Education), and the recovery key is saved in a location that is available to the domain or AAD administrator.
- If you sign in using a local account on a device running a business edition of Windows 10, you need to use the BitLocker Management tools to enable encryption on available drives.
On self-encrypting solid-state drives that support hardware encryption, Windows will offload the work of encrypting and decrypting data to the hardware. Note that a vulnerability in this feature, first disclosed in November 2018, could expose data under certain circumstances. In those cases, you’ll need a firmware upgrade for the SSD; on older drives where that upgrade is not available, you can switch to software encryption using the instructions in this Microsoft Security Advisory: Guidance for configuring BitLocker to enforce software encryption.
Note that Windows 10 and Windows 11 still support the much older Encrypted File System feature. This is a file- and folder-based encryption system that was introduced with Windows 2000. For virtually all modern hardware, BitLocker is a superior choice.
How do I manage BitLocker encryption?
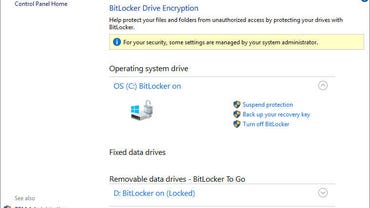
For the most part, BitLocker is a set-it-and-forget-it feature. After you enable encryption for a drive, it doesn’t require any maintenance. You can, however, use tools built into the operating system to perform a variety of management tasks.
The simplest tools are available in the Windows graphical interface, but only if you are running Pro or Enterprise editions. Open File Explorer, right-click any drive icon, and click Manage BitLocker. That takes you to a page where you can turn BitLocker on or off; if BitLocker is already enabled for the system drive, you can suspend encryption temporarily or back up your recovery key from here. You can also manage encryption on removable drives and on secondary internal drives. On a system running Windows Home edition, you’ll find an on-off button in Settings. In Windows 10, look under Update & Recovery > Device Encryption. In Windows 11, this setting is under Privacy & Security > Device Encryption. A warning message will appear if device encryption hasn’t been enabled by signing into a Microsoft account.
For a much larger set of tools, open a command prompt and use one of the two built-in BitLocker administrative tools, manage-bde or repair-bde, with one of its available switches. The simplest and most useful of these is manage-bde -status, which displays the encryption status of all available drives. Note that this command works on all editions, including Windows 10 Home.
For a full list of switches, type manage-bde -? or repair-bde -?
Finally, Windows PowerShell includes a full set of BitLocker cmdlets. Use Get-BitLockerVolume, for example, to see the status of all fixed and removable drives on the current system. For a full listing of available BitLocker cmdlets, see the PowerShell BitLocker documentation page.
How do I save and use a BitLocker recovery key?
Under normal circumstances, you unlock your drive automatically when you sign in to Windows 10 using an account that’s authorized for that device. If you try to access the system in any other way, such as by booting from a Windows 10 or Windows 11 Setup drive or a Linux-based USB boot drive, you’ll be prompted for a recovery key to access the current drive. You might also see a prompt for a recovery key if a firmware update has changed the system in a way that the TPM doesn’t recognize.
As a system administrator in an organization, you can use a recovery key (manually or with the assistance of management software) to access data on any device that is owned by your organization, even if the user is no longer a part of the organization.
The recovery key is a 48-digit number that unlocks the encrypted drive in those circumstances. Without that key, the data on the drive remains encrypted. If your goal is to reinstall Windows in preparation for recycling a device, you can skip entering the key and the old data will be completely unreadable after setup is complete.
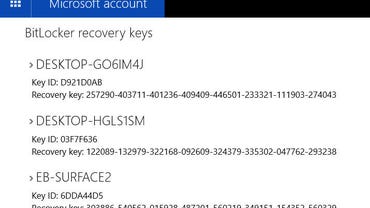
Your recovery key is stored in the cloud automatically if you enabled device encryption with a Microsoft account. To find the key, go to https://onedrive.com/recoverykey and sign in with the associated Microsoft account. (Note that this option works on a mobile phone.) Expand the listing for any device to see additional details and an option to delete the saved key.
If you enabled BitLocker encryption by joining your Windows 10 or Windows 11 device with an Azure AD account, you’ll find the recovery key listed under your Azure AD profile. Go to Settings > Accounts > Your Info and click Manage My Accounts. If you’re using a device that’s not registered with Azure AD, go to https://account.activedirectory.windowsazure.com/profile and sign in with your Azure AD credentials.
Find the device name under the Devices & Activity heading and click Get BitLocker Keys to view the recovery key for that device. Note that your organization must allow this feature for the information to be available to you.
Finally, on business editions of Windows 10 or Windows 11, you can print or save a copy of the recovery key and store the file or printout (or both) in a safe place. Use the management tools available in File Explorer to access these options. Use this option if you enabled device encryption with a Microsoft account and you prefer not to have the recovery key available in OneDrive.
Can I use BitLocker to encrypt removable drives?
Removable storage devices need encryption too. That includes USB flash drives as well as MicroSD cards that can be used in some PCs. That’s where BitLocker To Go works.
To turn on BitLocker encryption for a removable drive, you must be running a business edition of Windows 10. You can unlock that device on a device running any edition, including Windows 10 Home.
As part of the encryption process, you need to set a password that will be used to unlock the drive. You also need to save the recovery key for the drive. (It’s not automatically saved to a cloud account.)
Finally, you need to choose an encryption mode. Use the New Encryption Mode (XTS-AES) option if you plan to use the device exclusively on Windows 10. Choose Compatible Mode for a drive you might want to open on a device running an earlier version of Windows.
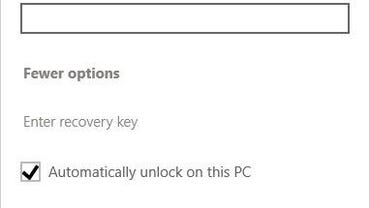
The next time you insert that device into a Windows PC, you’ll be prompted for the password. Click More Options and select the checkbox to automatically unlock the device if you want easy access to its data on a trusted device that you control.
That option is especially useful if you’re using a MicroSD card for expanded storage capacity on a device such as a Surface Pro. After you sign in, all of your data is immediately available. If you lose the removable drive or it is stolen, its data is inaccessible to the thief.
[ad_2]
Source link


