[ad_1]
Monster DDoS attacks hit Google Cloud and other major internet services. Google
Distributed Denial of Service (DDoS) attacks may be one of the least sophisticated types of cyberattacks but they can do real damage. Now Google and other top cloud companies are reporting new records for the largest DDoS attacks ever.
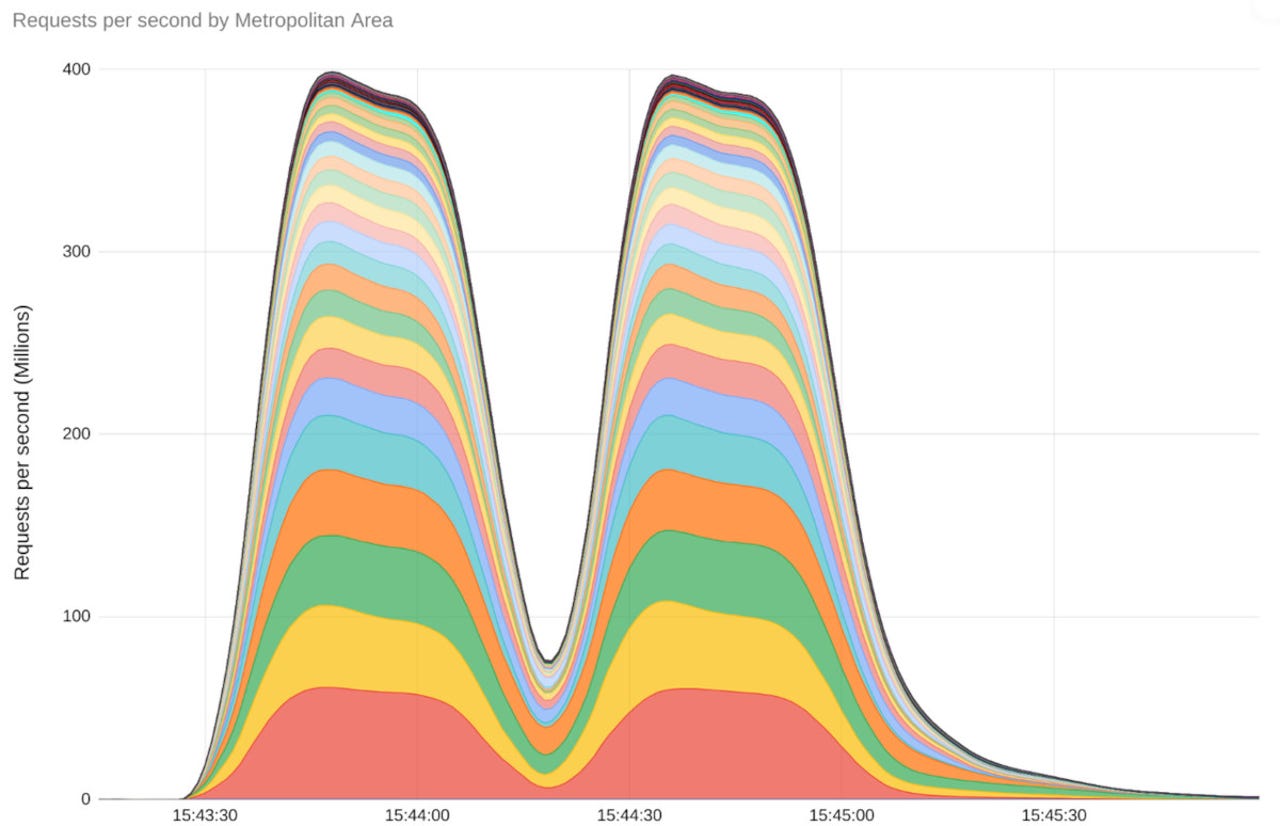
The Google Cloud was hit by the largest DDoS attack in history this past August, with the digital onslaught peaking at an unprecedented 398 million requests per second (RPS). How big is that? According to Google, in two minutes, the Google Cloud was slammed by more RPS than Wikipedia saw in all of September 2023.
Also: Newly discovered Android malware has infected thousands of devices
That’s big. The attack on Google Cloud, which employed a novel “Rapid Reset” technique, was 7½ times larger than any previously recorded DDoS attack. 2022’s largest-recorded DDoS attack peaked at “only” 46 million RPS.
Google wasn’t the only one to get hit. Cloudflare, a leading cloud delivery network (CDN), and Amazon Web Services (AWS), the world’s biggest cloud provider, also reported getting blasted. Cloudflare fended off a 201 million RPS attack, while AWS held off a 155 million RPS assault.
These DDoS attacks began in late August and “continue to this day,” according to Google, targeting major infrastructure providers. Despite the scale and intensity of the attacks, the top technology firms’ global load-balancing and DDoS mitigation infrastructure effectively countered the threat, ensuring uninterrupted service for their customers.
In the attacks’ wake, the companies coordinated a cross-industry response, sharing intelligence and mitigation strategies with other cloud providers and software maintainers. This collaborative effort developed patches and mitigation techniques that most large infrastructure providers have already adopted.
Also: The best VPN services (and how to choose the right one for you)
The “Rapid Reset” technique exploited the HTTP/2 protocol’s stream multiplexing feature which is the latest step in the evolution of Layer 7 attacks. This attack works by pushing multiple logical connections to be multiplexed over a single HTTP session.
This is a feature “upgrade” from HTTP 1.x, in which each HTTP session was logically distinct. Thus, just like the name says, an HTTP/2 Rapid Reset attack consists of multiple HTTP/2 connections with requests and resets one after another. If you’ve implemented HTTP/2 for your website or internet services, you’re a potential target.
In practice, Rapid Reset works by a series of requests for multiple streams being transmitted, followed immediately by a reset for each request. The targeted system will parse and act upon each request, generating logs for a request that is then reset, or canceled. Thus, the targeted system burns time and compute generating those logs even if no network data is returned to the attacker. A bad actor can abuse this process by issuing a massive volume of HTTP/2 requests, which can overwhelm the targeted system.
Also: New cryptographic protocol aims to bolster open-source software security
This is actually a turbo-charged version of a very old kind of attack: The HTTP flood request DDoS attack. To defend against these sorts of DDoS attacks, you must implement an architecture that helps you specifically detect unwanted requests as well as scale to absorb and block those malicious HTTP requests.
The vulnerability exploited by the attackers has been tracked as CVE-2023-44487.
Organizations and individuals serving HTTP-based workloads to the internet are advised to verify the security of their servers and apply vendor patches for CVE-2023-44487 to mitigate similar attacks. The patches are on their way. But, until they’re widely installed, I guarantee we’ll see more Rapid Reset attacks.
Most companies don’t have the resources needed to deal with such attacks. You need extensive and powerful network DDoS defensive services such as Amazon CloudFront, AWS Shield, Google Cloud Armor, or CloudFlare Magic Transit to fend off Rapid Reset attackers.
Eventually, the fix will be in for this particular attack, but similar ones will soon be on their way. As the security saying goes, “Security isn’t a product, it’s a process.”
[ad_2]
Source link

