[ad_1]
As Russia’s invasion of Ukraine continues for the third week, researchers have explored how cloud technologies are contributing to the conflict — at least, on the virtual battleground.
When Russia crossed into Ukraine in February, this triggered action online.
Ukraine had already experienced multiple attacks leading to website defacement, Distributed Denial-of-Service (DDoS) outages, and the use of destructive wiper malware. Anonymous hacktivists then became involved, and Ukraine’s government called for volunteers with cybersecurity skills to help protect critical infrastructure.
By March, Ukraine had started forming what officials called an “IT army” tasked with network defense — as well as offensive counterattacks against Russian threat actors.
According to new research conducted by Aqua Security’s Team Nautilus, cloud technologies now play a role in the digital side of the conflict.
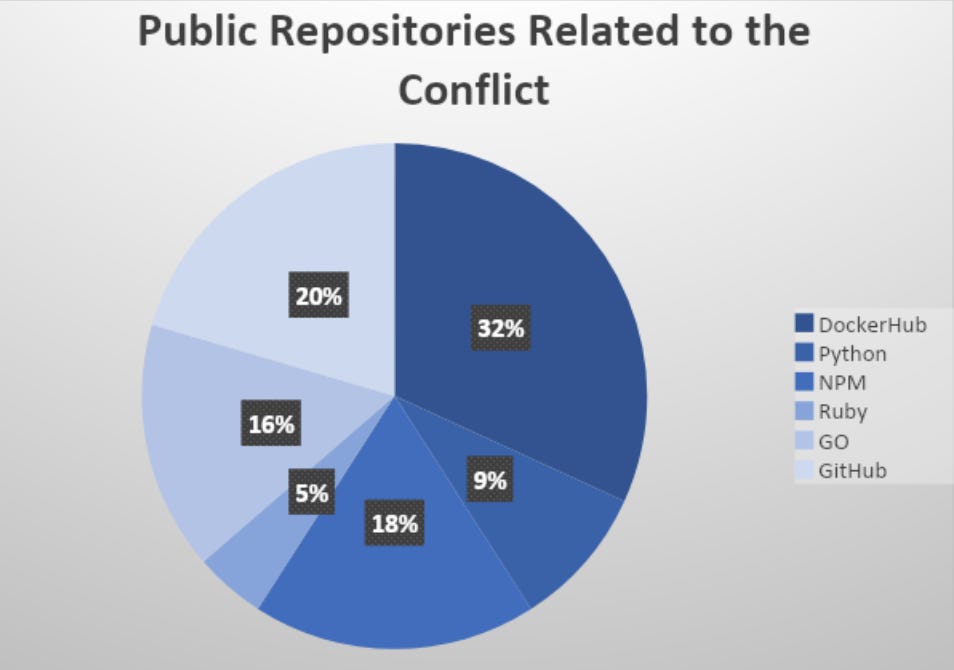
The team has tracked code and tools in public repositories, including Docker container images, code libraries, and popular software packages such as PyPI, npm, and Ruby.
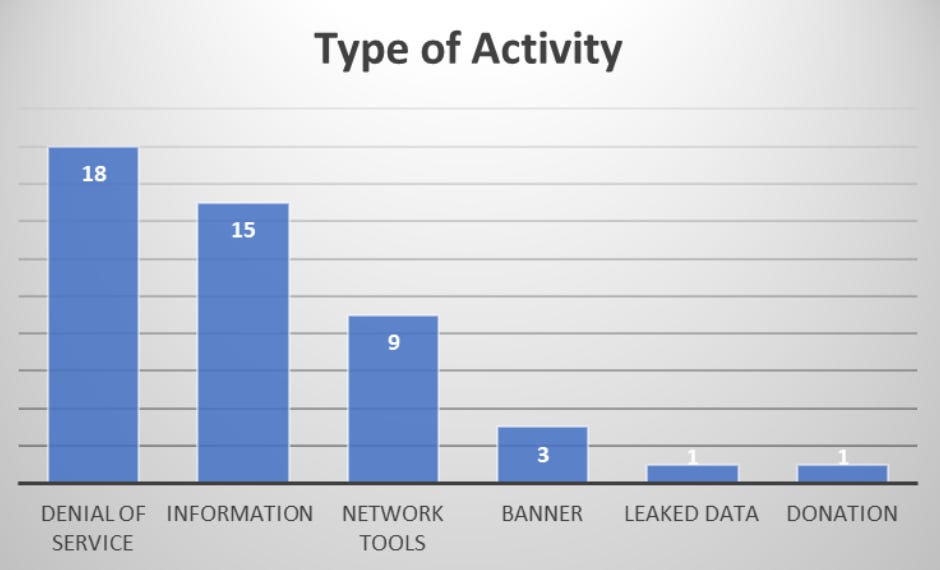
Team Nautilus searched for names, guides, and tools promoted for use in cyberattacks by either side. In total, roughly 40% of these public repositories were “related to denial-of-service activity aimed to disrupt the network traffic of online services,” according to the researchers.
Aqua Security
Aqua Security
Two container images, “abagayev/stop-russia:latest” and “erikmnkl/stoppropaganda:latest,” were of particular interest to the team. Both are DoS tools that contain how-to guides, expanding the potential of website disruption through cloud deployment to audiences without technical expertise.
Financial and multiple service providers in Russia are on the target list.
“Both container images also included attack tools that initiate DNS flood carried out over the UDP protocol, sending a large number of DNS requests to UDP in port 53, and aimed against Russian banks,” the team noted.
Honeypots deployed by Team Nautilus, set to gather data on IP addresses related to Russia and Ukraine, revealed that 84% of DDoS targets were affiliated with Russian IP addresses, whereas 16% were linked to Ukraine.
Overall, network and media organizations were attacked most often.
“As technology advances, experienced threat actors can create and distribute simple automated tools allowing less skilled individuals to join and participate in cyberwar,” the researchers say. “It also allows individuals and organized hacking groups to influence the conflict, using their knowledge and resources. We can see how emerging technologies are relevant in these efforts and can help make an impact.”
In related news, Google’s Threat Analysis Group (TAG) has taken down a “coordinated influence operation” linked to Belarus, Moldova, and Ukraine, and account protections have been ramped up for Ukrainian users suspected of being at higher risk of compromise due to the invasion.
Ukraine’s Computer Emergency Response Team for Ukraine (CERT-UA) previously warned that the Ghostwriter Belarusian threat group, also tracked as UNC1151, is actively spreading anti-NATO material and is involved in a number of phishing campaigns.
On March 11, the agency said malicious droppers, hosted in Discord servers, were also being served to victim organizations by UAC-0056. According to Palo Alto Networks, one victim was an energy company in Ukraine.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
[ad_2]
Source link

