[ad_1]
Microsoft has warned of new threats impacting blockchain technologies and web3 including “ice phishing” campaigns.
The blockchain, decentralized technologies, DeFi, smart contracts, exploration into the concept of a ‘metaverse‘ and web3 — the decentralized foundation built on top of cryptographic systems that underlay blockchain projects — are all being pursued in what could be radical changes in how we understand and experience connectivity today.
Read on: What is web3? Everything you need to know about the decentralized future of the internet
However, with every technological innovation, there may also be new avenues created for cyberattackers and web3 is no exception.
Today’s most common threats include mass spam and phishing conducted over email and social media platforms, social engineering, and vulnerability exploitation.
On February 16, the Microsoft 365 Defender Research Team said that phishing, in particular, has made its way over to the blockchain, custodial wallets, and smart contracts – “reaffirming the durability of these threats as well as the need for security fundamentals to be built into related future systems and frameworks.”
Microsoft’s cybersecurity researchers say that phishing attacks focused on web3 and the blockchain can take various forms.
One of the threats to watch out for is an attacker trying to obtain the private, cryptographic keys to access a wallet containing digital assets.
While emailed phishing attempts do occur, social media scams are rife. For example, scam artists may send direct messages to users publicly asking for help from a cryptocurrency service — and while pretending to be from a support team, they ask for the key.
Another tactic is by launching fake airdrops for free tokens on social media sites, and when users try to access their new assets, they are redirected to malicious domains that either try to steal credentials or execute cryptojacking malware payloads on a victim’s machine.
In addition, cybercriminals are known to conduct typo-squatting to impersonate legitimate blockchain and cryptocurrency services. They register website domains containing small errors or changes — such as cryptocurency.com rather than cryptocurrency.com — and set up phishing websites to steal keys directly.
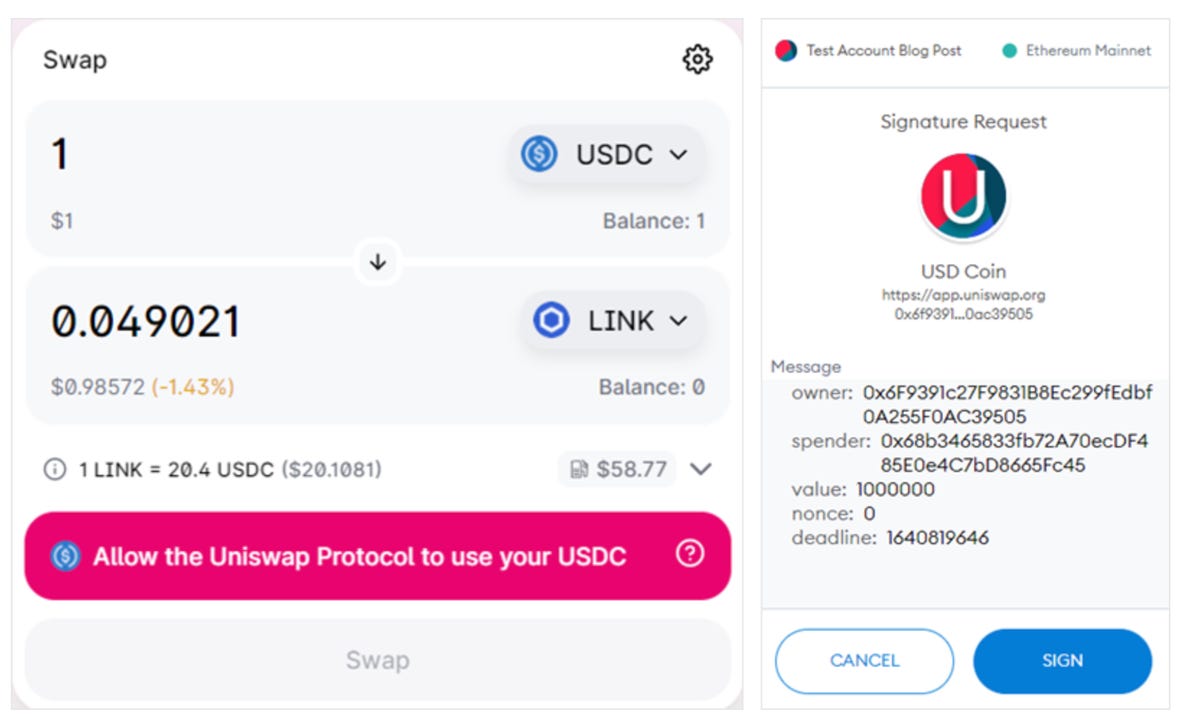
Ice phishing is different and ignores private keys entirely. This attack method attempts to dupe a victim into signing a transaction that hands over the approval of a user’s tokens to a criminal.
Such transactions can be used in DeFi environments and smart contracts to permit a token swap to take place, for example.
Microsoft
“Once the approval transaction has been signed, submitted, and mined, the spender can access the funds,” Microsoft noted. “In case of an ‘ice phishing’ attack, the attacker can accumulate approvals over a period of time and then drain all victim’s wallets quickly.”
The most high-profile example of ice phishing is last year’s BadgerDAO compromise. Attackers were able to compromise the front-end of BadgerDAO to obtain access to a Cloudflare API key, and malicious scripts were then injected — and removed — from the Badger smart contract.
Customers with high balances were selected and they were asked to sign fraudulent transaction approvals. BadgerDAO said in a post-mortem of the phishing attack that “the script intercepted web3 transactions and prompted users to allow a foreign address approval to operate on ERC-20 tokens in their wallet.”
“After phishing a number of approvals, a funding account sent 8 ETH to the exploiter’s account to fuel a series of transferFrom calls on the users’ approved tokens,” BadgerDAO said. “This allowed the attacker to move funds on behalf of the users to other accounts, which then liquidated the funds and exited via the Badger Bridge to BTC.”
Approximately $121 million was stolen. An audit and recovery plan is underway.
“The Badger DAO attack highlights the need to build security into web3 while it is in its early stages of evolution and adoption,” Microsoft says. “At a high level, we recommend that software developers increase security usability of web3. In the meantime, end-users need to explicitly verify information through additional resources, such as reviewing the project’s documentation and external reputation/informational websites.”
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
[ad_2]
Source link

